A massive Capital One data breach has released sensitive information impacting more than 100 million people in the US and 6 million Canadians.
On July 29, the FBI arrested Paige A. Thompson, accusing her of downloading almost 30 GB of credit application data from a rented cloud server. The data included roughly 80,000 bank account numbers, 140,000 Social Security numbers, and one million Social Insurance Numbers from Canadian Capital One customers.
Thompson was implicated as the culprit after her name was publicly listed on a GitHub page connected to the attack. Capital One also connected an IP address associated with the attack to the virtual private network (VPN) services to Thompson. It is believed that Thompson used web app firewall credentials to obtain privilege escalation to access the information.
Capital One received an email linking to Thompson’s GitHub page claiming the company had been hacked. Under further examination, a file timestamped April 21, 2019, made it apparent the data was stolen after accessing a server through a misconfigured firewall.
The theft was an insider attack
Considered an insider threat as she was employed by the web hosting company involved in the breach, Thompson used web app firewall credentials to obtain privilege escalation to access the information, according to court documents released by the FBI. Her GitHub page includes her CV, which cites her most recent work experience as a systems engineer for AWS from May 2015 to September 2016.
The FBI claims Thompson used a Meetup group that was visible to the public to encourage others to join a Slack channel named “Netcrave Communications.” Brian Krebs, one of the most widely respective security experts in the field, gained access to the channel.
“One of the more interesting posts by Erratic [Thompson] on the Slack channel is a June 27 comment listing various databases she found by hacking into improperly secured Amazon cloud instances,” Krebs wrote.
A Twitter account is believed to be associated with Thompson under the name “ᗴᖇᖇᗩ丅Ꭵᑕ” (@0xA3A97B6C). The account showed tweets from within the past 90 days also describing databases she found by hacking into AWS cloud instances.
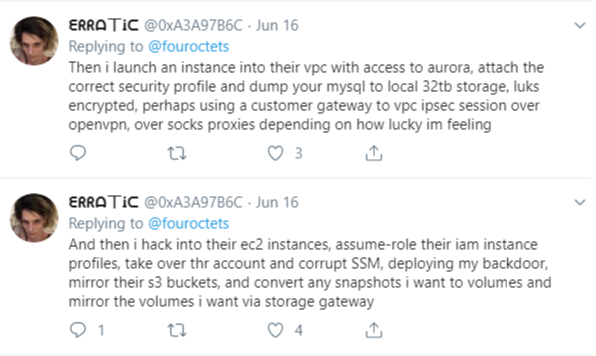
Image via KrebsOnSecurity
In addition to a number of cybercrimes, Erratic also frequently posted descriptions of struggling with depression, unemployment, and gender identity.
It’s not believed her intentions were to make money from the hack, but it’s highly likely some individuals connected to Thompson were motivated by profit.
Unanswered questions
It is still unknown which additional databases or systems Thompson gained access to.
One circulating Slack post implies Thompson may have hacked into a number of systems. The screenshot lists additional files and mentions a number of suspicious tape archive files, some of which include the names of other large companies.
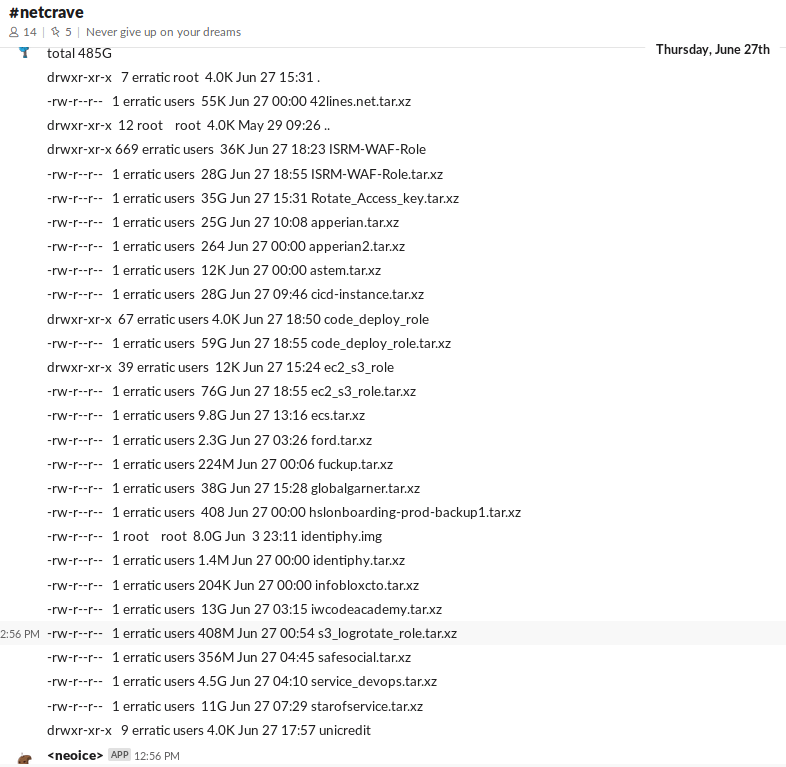 Image via KrebsOnSecurity
Image via KrebsOnSecurity
In another post on Slack, Thompson calls out the Infoblox file specifically, noting it contained more than 500 Docker containers. A few other comments depict Thompson as unsure of what to do with the data she had uncovered.
The court documents note these discussions, but do not imply Thompson was in possession of or attempting to sell sensitive information belonging to other companies.
The value of stolen data
Luckily, for consumers, no credit card account numbers or credit-related login credentials were compromised. Still, at least 120,000 Social Security numbers were accessed and were not encrypted or tokenized.
While the information may not have been sold by Thompson, other actors may have obtained it while it was stored outside AWS.
For reference, below are some figures related to the value of sensitive information online:
These are general price averages someone on the dark web would pay for an individual’s information, according to Experian.
- Social Security number: $1
- With CVV number: $5
- With bank info: $15
- Subscription services: $1–$10
- Loyalty accounts: $20
- Driver's license: $20
- Credit or debit card (credit cards are more popular): $5–$110
- Online payment services login info (e.g., PayPal): $20–$200
- Diplomas: $100-$400
- Passports (US): $1,000–$2,000
- Medical records: $1–$1,000
These are fairly subjective figures, but they can help to paint the picture of the enormous value presented to hackers, motivating attacks for profit.
Looking forward
Capital One responded to the incident by explaining it will notify individuals impacted by the breach and will provide free credit monitoring and identity protection to victims.
“Safeguarding our customers' information is essential to our mission and our role as a financial institution. We have invested heavily in cybersecurity and will continue to do so,” the press release described. “We will incorporate the learnings from this incident to further strengthen our cyber defenses.”
As of the market closure on July 30, 2019 — the day the breach became public — the value of Capital One Financial Corp. stock fell nearly 6% from $96.92 to $91.06.
Thompson is charged with one count of computer fraud with a maximum penalty of five years in prison and a $250,000 fine. The case is listed as U.S. v. Thompson, 19-mj-344, U.S. District Court, Western District of Washington (Seattle).
Thompson is being held in police custody until her bail hearing which is set to take place on August 1.
Attacks like these can often be prevented with properly configured web application firewalls and solutions such as cloud workload protection platforms and network security policy management software.



 by Aaron Walker
by Aaron Walker
 by Aaron Walker
by Aaron Walker
 by Aaron Walker
by Aaron Walker