In an interconnected world where cyber threats loom, mobile device management (MDM) software emerges as the valiant shield.
MDM software defends organizations against data breaches, malicious intrusions, and unauthorized access, ensuring that the secrets of the digital realm remain safe and sound within the confines of impenetrable mobile fortresses.
What is mobile device management software?
Mobile device management (MDM) software is a robust solution designed to enable organizations to efficiently manage and secure their fleet of mobile devices, including smartphones, tablets, and laptops, from a centralized platform.
It gives administrators granular control over device configurations, application distribution, and security policies. It allows them to enforce strong security measures, track device usage, remotely wipe data if necessary, and ensure compliance with organizational standards and regulatory requirements.
This comprehensive software empowers businesses to streamline device management, enhance data protection, and mitigate security risks, ultimately fostering a productive and secure mobile environment. The most crucial feature companies should prioritize is security.
The article will explore security features in mobile device management software and top recommended software solutions for each feature.
Security is the name of the game
Security features are vital in mobile device management (MDM) as they protect sensitive data, mitigate security risks, ensure compliance, enable centralized control, and facilitate incident response.
With robust encryption, remote lock or wipe capabilities, threat detection, and standardized security policies, MDM software creates a secure environment for mobile devices, safeguarding confidential information and reducing the risk of unauthorized access or data breaches. This enhances productivity, helps organizations meet regulatory requirements, and responds effectively to security incidents.
However, there is almost no public information on which MDM software has the best security rating. Luckily, G2 can share this data on which MDM software is the most secure by each security feature.
G2 asked reviewers to rate products in the Mobile Device Management category on each of the security features below:
- Security: Protects employees, company, and data from potential vulnerabilities or malware
- Applications Consolidation: Separates work apps and data from personal apps and data
- Applications Management: Centrally manages, configures, and oversees applications on employees' mobile devices
- Blacklist: Implements blacklist policy to block unwanted or suspicious applications
- Whitelist: Implements whitelist policy to easily and securely deploy recommended or required applications
Recommending MDM platforms based on G2’s Grid® Report data
The Spring 2023 G2 Grid® Report for MDM Platforms can help software buyers find the right software based on Security, Application Consolidation, Remote Wipe, Blacklist, Whitelist, and Applications Management.
Security
MDM security protects mobile devices by implementing device security policies, controlling application installation, utilizing mobile threat detection, and managing patch distribution.
These measures fortify devices against unauthorized access, prevent the infiltration of malicious apps, proactively identify and neutralize security threats, and ensure devices are up-to-date with essential security updates. This comprehensive approach safeguards sensitive data and mitigates the risk of breaches, providing a secure environment for mobile devices.
G2 asks reviewers to rank MDM software based on “Security.” The top five solutions by this metric are mentioned below.

With a category average of 91%, Jamf Now leads by 99%, followed by Miradore, Rippling, Hexnode UEM, and Kandji.
IT management professionals who want MDM software to focus on this feature should explore these five products.
Application Management and Consolidation
MDM is crucial in application management and consolidation by providing centralized distribution, version control, blacklisting or whitelisting capabilities, license tracking, and mobile app containerization.
Administrators can efficiently deploy and manage applications across devices through a centralized console, ensuring employees can access the necessary software. MDM also helps maintain application security by controlling versions and preventing unauthorized or harmful applications from being installed.
Organizations can optimize their app inventory and ensure compliance by tracking licenses and usage. Additionally, mobile app containerization enhances security by isolating business applications and data and protecting sensitive information from potential risks.
G2 asks reviewers to rank MDM software based on “Application Management" and “Application Consolidation.” The top four solutions by this metric are mentioned below.
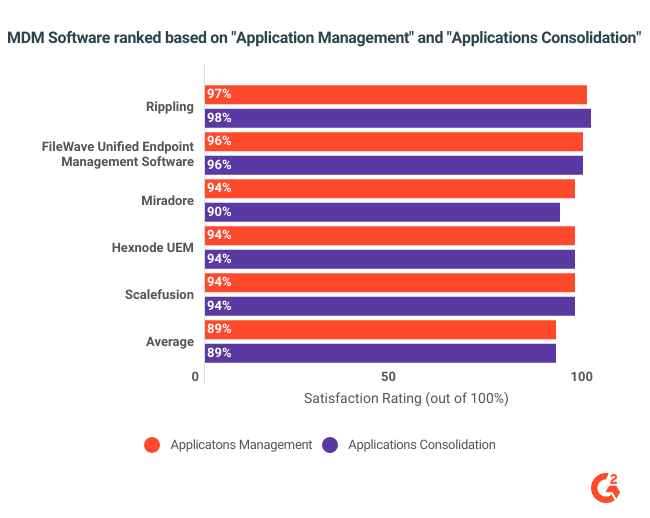
With a category average of 89%, Rippling leads with 97% in application management and 98% in application consolidation, followed by FileWave Unified Endpoint Management Software, Miradore, Hexnode UEM, and Scalefusion.
IT management professionals who want MDM software to focus on application management features should explore these four products.

Whitelist and Blacklist
A whitelist is a list of approved applications permitted on the devices, while a blacklist consists of prohibited applications blocked from installation or usage.
Whitelisting ensures that only authorized applications are allowed, minimizing the risk of malicious or unauthorized software, while blacklisting prevents the installation or use of known malicious or non-compliant applications.
Both mechanisms provide administrators with control over the application ecosystem, enhancing security and protecting devices and data from potential threats.
G2 asks reviewers to rank MDM software based on “Whitelist" and “Blacklist.” The top four solutions by this metric are mentioned below.
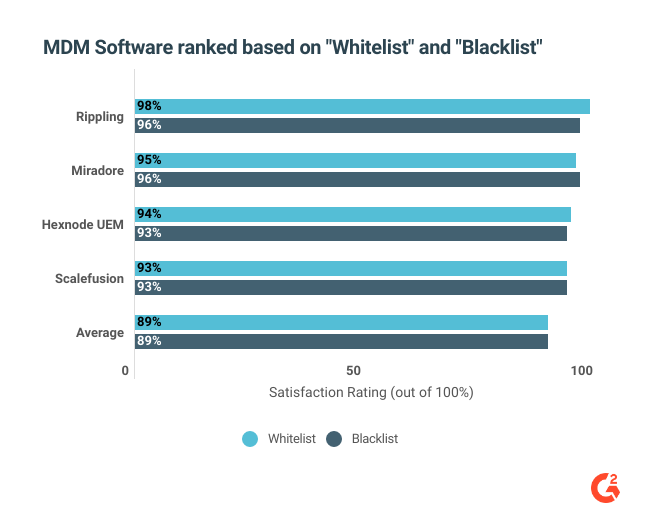
With a category average of 89%, Rippling leads with 98% in the whitelist and 98% in the blacklist, followed by Miradore, Hexnode UEM, and Scalefusion.
IT management professionals who want MDM software to focus on application management features should explore these four products.
Safeguarding data and securing devices
In summary, MDM software enables efficient device and application management by shielding sensitive data, mitigating security risks, and ensuring compliance.
With its robust security measures, centralized control, and comprehensive monitoring capabilities, MDM empowers organizations to protect employees, safeguard company assets, and maintain the integrity of critical data.
By embracing MDM, organizations can confidently navigate the mobile landscape, fostering productivity and innovation while fortifying their defenses against evolving security threats.
Learn more on how to purchase an MDM solution with G2's MDM Buyer’s Guide.
Edited by Shanti S Nair


 by Tian Lin
by Tian Lin
 by Tian Lin
by Tian Lin
 by Tian Lin
by Tian Lin