Data loss prevention (DLP) security has significantly changed over the last few years.
These changes are driven by the ever-evolving landscape of cyber threats, the shift towards more complex IT environments, and various innovations that have appeared as vendors have developed new solutions.
As businesses increasingly migrate to cloud services and remote work has become the norm, the need for robust DLP strategies has intensified.
Ultimately, all cybersecurity is “about'' data security, and your organization can’t have a solid security strategy without smart data security at its core.
Legacy DLP’s limited focus fails to keep pace with today’s security threats
Historically, DLP systems focused on securing the enterprise network perimeter under the assumption that threats primarily came from outside the network, and once inside, users were trusted.
However, this approach has become insufficient with the rise of insider threats and the blurring of network boundaries.
According to a report by IBM Security and Ponemon Institute, the average total cost of a data breach in 2022 was over $4 million, a figure that has been steadily increasing over the years. Another study by IBM Security found that in 2022, the average cost rose to $4.75 million per incident, highlighting the growing financial implications of data breaches.
Data security is a core need for any security strategy or practice and is the key tenet that originated all cybersecurity offerings.
Early DLP systems monitored and controlled data transfer based on predefined policies
These policies would typically include rules to block the transfer of sensitive information outside the corporate network.
While effective against certain threats, these rule-based DLP systems had several technical limitations:
- Static rules couldn’t easily adapt to the dynamic nature of data.
This leads to a high number of false positives and negatives. The static nature meant that as data use evolved, the rules would quickly become outdated unless constantly revised.
- Limited contextual awareness reduced accuracy.
Early DLP solutions often lacked the context needed to make accurate decisions about data transfers. They would block or allow transfers based solely on simplistic criteria without understanding the nuances of data usage patterns.
- Hyper focused on perimeter security.
They assumed that threats would be stopped at the perimeter, a presumption that is no longer valid in today's landscape, where the perimeter has all but dissolved due to the rise of mobile, cloud computing, and remote work.
- Suffered from complexity and scalability.
The systems were often complex to manage and not easily scalable. As organizations grew and the amount of data exploded, these systems struggled to keep up without significant manual intervention.
- Ineffective for data outside the network.
These DLP systems did not effectively protect data once it left the network perimeter, such as data shared with partners or stored on a remote employee's device.
Many of those features, which pose limitations, made legacy data security via DLP solutions either impossible to implement or a source of discontent for users and administrators, as valid data security requests were often denied due to simple misconfiguration.
Despite the risks associated with data breaches, companies struggled to find value in DLP
However, due to past issues with DLP as a sole solution for data security, buyers have historically hesitated to engage or honor longer-term contracts with data security vendors.
This occurs even though the time to value and return on investment (ROI) data indicates that more time for implementation is exactly what is needed to truly get value from a data security solution.
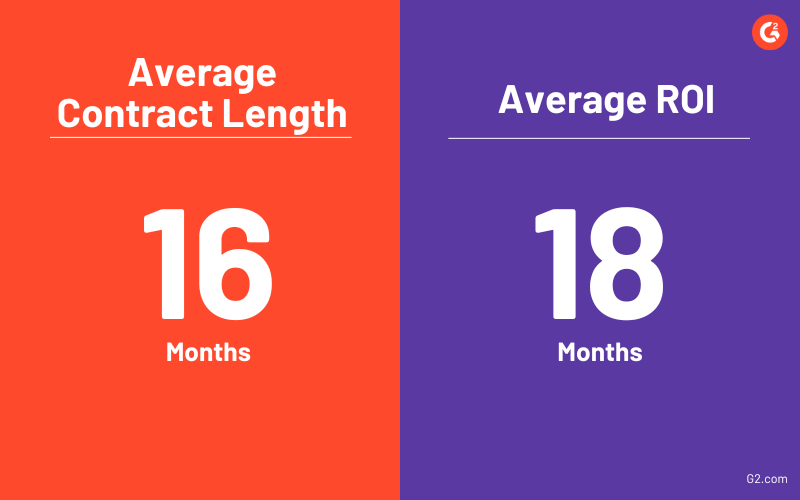
Digging deeper into G2 category data, we see that, on average, it takes 18 months for users to get ROI for DLP products. However, the average contract length is 16 months.
Vendors can experience a significant increase in user satisfaction and renewal rates if they suggest increasing their contract duration to 18 months or above. Buyers should be aware of this insight and be willing to extend their contracts to realize the full value of these solutions.
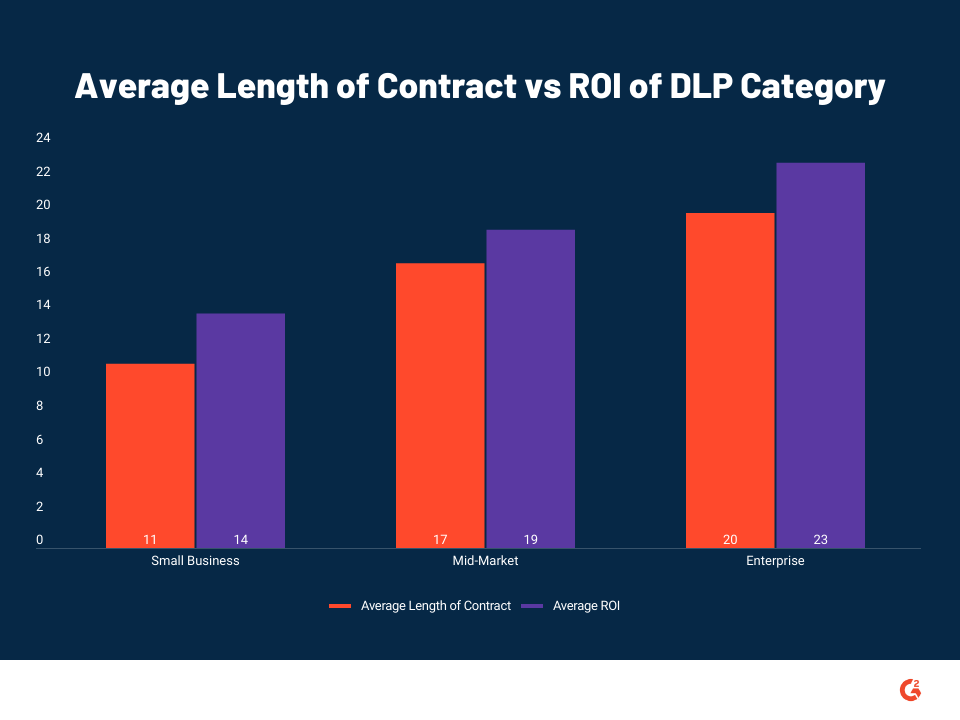
The company segment breakdown of the reviews tells the same story.
As shown in the above graph, reviews of all company segments mention the average length of contract duration is lower than the number of months it takes to get a return on investment for DLP products.
To be blunt, give it time to get the value you seek in data security solutions.
Modern DLP solutions address old challenges
DLP solutions have evolved from rule-based systems to more advanced platforms incorporating machine learning and artificial intelligence in response to these challenges.
These technologies enable DLP systems to learn from data patterns, improving the detection of potential threats and reducing false positives. For instance, statistical models can analyze typical user behavior, and any deviation that may indicate a data exfiltration attempt can trigger an alert or an automatic response.
Today:
- “Ease of use” guides DLP decisions: According to G2 data, 23% of reviewers switch to a new DLP product due to product feature set and 20% due to ease of use, hinting how crucial both factors are for user satisfaction.
Over time, that acceptance and happiness with data security vendors’ offerings have improved. This results from improved user experience and more policy engine capabilities via vendor solutions.
- Integration is possible with other security systems: Modern DLP solutions are now part of a broader security strategy that integrates with other tools such as encryption, multi-factor authentication, and security information and event management (SIEM) systems.
This integrated approach ensures that data protection measures are in place throughout the data lifecycle, from creation to transmission, storage, and eventual deletion.
- DLP plays an integral role in zero trust: In the context of "zero trust," which operates on the principle of "never trust, always verify," data security has always been a key tenet. Zero trust architectures assume that threats exist both outside and inside the network.
Therefore, DLP and data security solutions must monitor and control data movement across the organization's entire digital environment, regardless of where the data resides or where it is going.
Remember that zero trust requires a smart approach to data security. Without great insight and analytics into the data across your systems and infrastructure, you cannot achieve it.
Innovative solutions that have modernized DLP
Several companies have emerged as leaders in the new generation of DLP and data security-specific solutions. The vendors on this list are those that are most noted in G2’s research areas but are in no specific order of “ranking.”
These vendors have been noted for providing their customers with unique and innovative solutions directly related to the G2 security taxonomy classifier. Your organization should take a deeper look at the vendors in our taxonomy, including:
- Broadcom: Symantec's DLP solutions are recognized for their comprehensive data protection capabilities across endpoint, network, and cloud environments.
- McAfee: McAfee provides a DLP product that integrates with their cloud access security broker (CASB) for enhanced data protection in cloud environments.
- Fortra's Digital Guardian: Offering a data-centric approach to security, Digital Guardian's platform is known for its strong data visibility and flexible controls.
- Forcepoint: Forcepoint's DLP solutions include behavioral analytics to understand how users interact with data, providing more nuanced controls and protection.
- Varonis Data Security Platform: Specializing in data security and analytics, Varonis offers solutions that use machine learning to detect unusual activity and prevent data breaches.
- Nightfall AI: Nightfall AI is a startup leveraging machine learning to discover, classify, and protect sensitive data across cloud services and infrastructure. Its platform is particularly suited to identifying and securing data in SaaS and IaaS environments.
- BigID: BigID uses advanced machine learning and identity intelligence to help organizations better protect their customer and employee data and meet privacy regulations. They provide a data intelligence platform for privacy, protection, and perspective on personal data.
- Securiti: Securiti is a startup offering a PrivacyOps platform that helps automate privacy compliance with regulations like GDPR and CCPA. They use AI to identify sensitive data across systems, enabling companies to handle data subject requests and remediate risks better.
- Atakama File Encryption: Focusing on securing data at the file level, Atakama’s solution encrypts each file individually and requires multi-factor authentication for file access, thereby reducing the risk of mass data exfiltration.
- Unbound Security: Dyadic Security, also known as Unbound Tech, introduces a novel approach to data security using secure multiparty computation to ensure cryptographic keys are never in one place at a time, making it virtually impossible for attackers to steal them in a usable form.
- Inpher.io: Inpher has developed cryptographic secret computing technology for secure analytics and machine learning. Their solution enables analytics and machine learning models to run directly on encrypted data.
- Satori Data Security Platform: Satori Cyber provides a secure data access cloud that simplifies how organizations govern and secure their data. It's designed to be compatible with the most widely used data stores and SaaS applications.
- VGS Platform: Very Good Security (VGS) provides a platform that secures sensitive data, allowing businesses to operate on de-identified data and offload the risk. They provide an intriguing approach by enabling companies to derive value from sensitive data without actually handling it, which they call “data aliasing”.
- Nullafi: Nullafi offers a real-time data aliasing platform that secures sensitive data by aliasing it both at rest and in transit. Their solution allows businesses to protect private information such as PII, PHI, and financial data by shielding it from unauthorized access, which is essential for compliance and data privacy. With their technology, only aliased data is used in daily operations, while real data is kept safe, significantly reducing the risk of a data breach.
- Strac: Strac offers a DLP product that eliminates data leakage from endpoint and SaaS applications. Their solution comes with a no-code scanner that detects, blocks, and redacts PII, PHI, and other types of sensitive data. It comes with AI features offering greater accuracy in detecting sensitive data across unstructured text and documents, including jpeg, png, pdf, docx, and doc.
These mega-vendors and startups are contributing to the future of DLP and data security through a mix of proprietary technologies, machine learning algorithms, and innovative encryption techniques.
As they grow and their technologies mature, they are expected to offer significant competition to the incumbents and may become attractive acquisition targets for larger companies looking to bolster their data security offerings.
Advanced analytics and integration define DLP’s evolution
Looking forward, we can expect DLP and data security technology to evolve further with the adoption of advanced analytics, deeper integration with cloud platforms, and the development of standards for seamless interoperability among various security solutions.
Additionally, as regulatory compliance becomes more stringent globally, data security solutions will be critical in helping organizations meet their legal obligations regarding data protection.
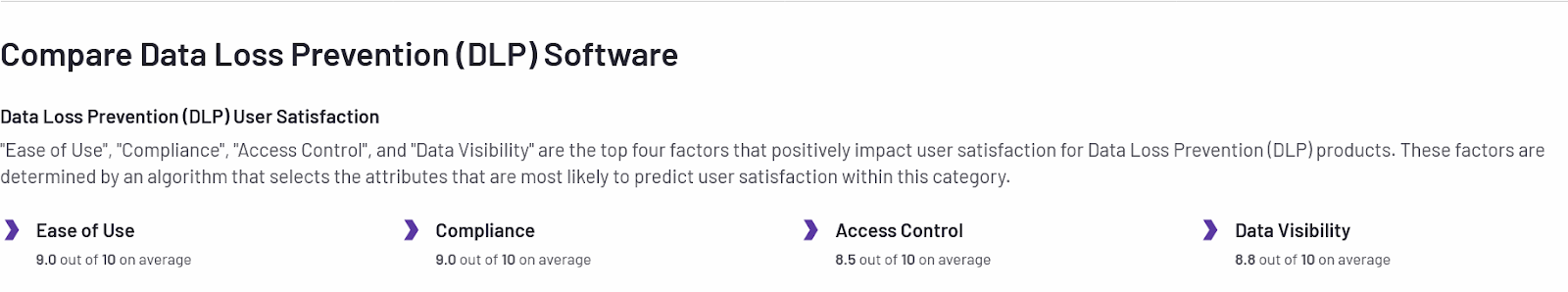
Consider the following data as you evaluate data security and DLP-like solutions. These are the key issues buyers seek to get value from and are key to evaluating these solutions.
Ensure DLP is part of your zero trust framework
The evolution of DLP security is a testament to the dynamic nature of cyber threats and the necessity for continuous innovation in cybersecurity.
As part of an effective security strategy, especially within a zero trust framework, DLP remains critical in protecting an organization's most valuable asset—its data.
Companies that offer innovative solutions will lead the way in helping organizations navigate the complex security landscape of the future.
Learn more by watching our inaugural episode of “Security Snippets”—a new series from G2’s Market Research team.
 This article is co-written by Amal Joby, G2 market research analyst, cybersecurity.
This article is co-written by Amal Joby, G2 market research analyst, cybersecurity.
Edited By Jigmee Bhutia
.png?width=500&name=Light%20(5).png)
.png?width=500&name=Light%20(5).png)
 by Aaron Walker
by Aaron Walker
 by Dr. Chase Cunningham
by Dr. Chase Cunningham
 by Lauren Worth
by Lauren Worth