This post is part of G2's 2025 digital trends series. Read more about G2’s perspective on digital transformation trends in an introduction from Tim Sanders, VP, research insights, and additional coverage on trends identified by G2’s analysts.
No magic bullets for security: strategy and AI scaling will be key
Prediction
While vendors push new solutions and “innovative” technologies to solve future security problems, most threat tactics will simply be revisions to old actions that still work for the majority of attacks, especially against small businesses.
With cyber threats becoming increasingly sophisticated, organizations are shifting toward signal-based threat detection and response to safeguard their systems more effectively. It’s crucial to remember that older, well-known threats still pose significant dangers, and most still work.
Many organizations, especially SMBs, often get distracted by new, flashy threats that vendors highlight yet fail to address older vulnerabilities that remain highly relevant.
By combining insights from advanced AI-driven security solutions with a focus on addressing both emerging and existing threats, organizations can take a more holistic approach.
Signal aggregation platforms empower businesses to prioritize security efforts intelligently, ensuring that they tackle both legacy vulnerabilities and new threats in a balanced manner rather than chasing only the latest risks vendors promote.
While 4 in 5 buyers care about vendors' history of security incidents, nearly half say they purchase software without security assessments
In 2025, we can expect a growing trend in which organizations place increasing importance on the security history of vendors, but a significant gap between awareness and action will persist.
While most buyers will continue to care about vendors' history of security incidents, nearly half may still purchase software without conducting thorough security assessments. This disconnect suggests that convenience, budget pressures, or time constraints will continue to drive hasty purchasing decisions. See the graphic below from the buyer behavior report.
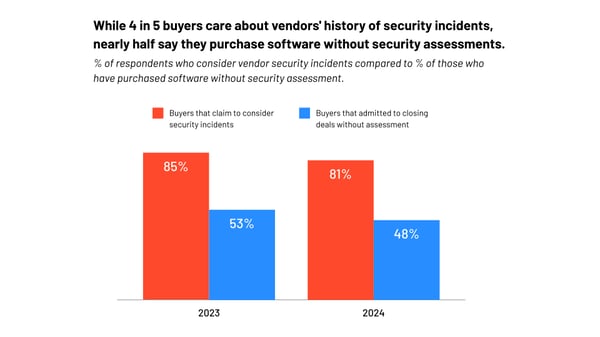
However, as cyber threats escalate and the costs of security breaches rise, regulatory pressures, industry standards, and more publicized breaches will push businesses to close this gap, making comprehensive security assessments a non-negotiable part of the purchasing process.
In 2025, cybersecurity will be dominated by the continued rise of AI-driven attacks and defenses, as well as the broad adoption of zero trust architecture (ZTA).
Sophisticated AI models will be used to launch automated, adaptive attacks that can exploit system vulnerabilities at scale. On the defensive side, AI will be critical in threat detection, response automation, and predictive analytics to stay ahead of emerging threats.
Zero trust, which gained prominence in the early 2020s, will solidify as the foundational security model for organizations seeking to minimize the risks of unauthorized access and insider threats, particularly in cloud environments.
The rapid migration to cloud services and hybrid work models, accelerated by the COVID-19 pandemic, has exposed traditional perimeter-based security as insufficient, making zero trust a necessity.
The days of ignoring security and hoping a breach doesn’t occur are over
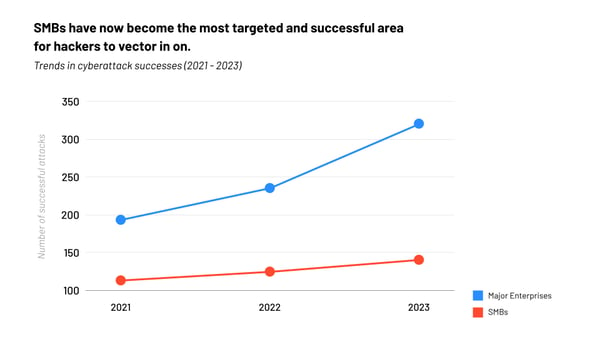
In 2025, the era of disregarding cybersecurity and hoping for the best will be a thing of the past. Businesses, particularly small and medium-sized enterprises (SMBs), will be forced to confront the harsh reality that they are prime targets for cyberattacks.
As the global economy becomes more interconnected, SMBs serve as essential cogs in the supply chains of larger corporations, making them attractive targets for hackers. Cybercriminals often see SMBs as "soft targets" due to their comparatively lower investment in security measures.
As ransomware-as-a-service and other attack vectors proliferate, SMBs will face growing pressure to not only invest in basic cyber hygiene but to implement advanced threat detection and response solutions, including AI-driven defenses and zero trust architectures. These solutions will become more accessible to smaller businesses as vendors and service providers tailor their offerings to meet the unique challenges faced by SMBs, including limited budgets and smaller IT teams.

The regulatory landscape in 2025 will impose greater accountability on SMBs to protect customer data and ensure compliance with industry standards. Governments and industry bodies will implement more stringent regulations, requiring SMBs to adopt a proactive security posture.
2025: A wake-up call for SMBs to prioritize cybersecurity
One of the key trends for 2025 will be the increased targeting of SMBs by ransomware and supply chain attacks. Hackers understand that SMBs often lack the advanced cybersecurity infrastructure of larger enterprises, making them easier to exploit.
As cybersecurity becomes a business-critical function, SMBs will need to prioritize security investment, collaborate more closely with third-party experts, and cultivate a culture of security awareness across their organizations.
In short, 2025 will be the year SMBs fully embrace the reality that cybersecurity is no longer optional but a necessary component of business survival in an increasingly hostile digital landscape.
Learn more about the evolutions of zero trust, SSE, and SASE!
Edited by Jigmee Bhutia


 by Dr. Chase Cunningham
by Dr. Chase Cunningham
 by Dr. Chase Cunningham
by Dr. Chase Cunningham
 by Dr. Chase Cunningham
by Dr. Chase Cunningham