Meet Mira.

Mira is the most wonderful three-legged doggo who loves to bark at everything. The butterfly sitting outside, a car passing by, or the Amazon delivery person ringing your doorbell, you can trust Mira to be on the job, bark at the noise, and be alert 24/7. Well, this is a blog about G2’s newest category, Zero Trust Platforms, so why are we talking about Mira? Read on to find out!
G2 is excited to announce the category launch of zero trust platforms, a cybersecurity framework built on the principle of “never trust, always verify.”
What is zero trust?
Zero trust is a strategic security concept and framework built on the principle that no implicit trust is granted to entities, assets, user accounts, or digital assets or connections based solely on simple factors. These factors include physical or network location, such as local area networks vs. the internet, or asset ownership, like enterprise or personally owned, depending on the policy configuration.
Zero trust: From concept to creation
The concept of zero trust was first introduced in 2009 when a former Forrester analyst, John Kindervag, first used the term. John Kindervag developed the idea of needing to authenticate all entities regardless of their location as a response to the reduced efficiency of perimeter-based security models. The concept of zero trust places more importance on the value of least privilege and strict identity verification.
Tip: The concept of "least privilege" is a cybersecurity principle that dictates that users, applications, and systems should only have the minimum level of access or permissions necessary to perform their tasks or functions. Users have their access restricted only to the bare essentials required to do a job and nothing more.
Along with the least privilege principle, a key concept of zero trust is around identity access management (IAM). Traditional security models initially focused on network parameters, risk-based analysis, and encryption.
Zero trust takes this a step further by including identity verification at the crux of it all. This includes ensuring strong IAM principles, multi-factor authentication (MFA), single sign-on (SSO), role-based access control, user-based analytics, and identity federation.
Below are some of the core components that make up zero trust platforms.
Zero trust networking: Slow but steady wins the race
G2’s first step into the zero trust world began with the creation of the Zero Trust Networking category. We made a comparison of the average time to ROI (in months) with several other security categories of G2 that form the core of zero trust platforms—Encryption, Security Orchestration, Automation, and Response (SOAR), Microsegmentation, Endpoint Detection & Response (EDR), and IAM.
The data shows us that zero trust networking software takes the longest time to achieve ROI, which indicates that customers are waiting much longer to see value in their investment compared to other security software available. This is driven by a variety of factors:
- Complexity in implementing strategy: Understanding the concept of zero trust is one thing, but implementing it is a whole other ball game. The complexity of introducing a new cybersecurity framework is a hassle for many customers.
- Legacy infrastructure: According to a 2022 Zero Trust survey by General Dynamics, 58% of the respondents listed legacy technology issues as the number one barrier to implementing zero trust.
- Poor UX: Imagine having to verify with “I am not a robot” multiple times a day.
- Scalability concerns: As companies grow and expand, the number of devices—mobiles, laptops, servers, storage, etc., increases. Under the concept of zero trust, each device needs to be continuously verified, and managing scalability becomes a major cause for concern.
Zero trust isn't a one-step approach to security but an amalgamation of every single security principle in a framework that depends on consistently verifying each user and application.
Although zero trust has evolved from being a concept into an important security framework, it's still a work in progress, or should I say, a work of art, in progress. There is no doubt that companies across the globe are looking to implement it in their security strategies, but there are still hurdles to overcome.
In G2’s 2024 Buyer Behavior Report, a surprising 48% of survey respondents admitted to closing software purchases without their vendor of choice completing a security or privacy assessment. This represents a 33% cognitive dissonance gap between buyers who claim to care about security and privacy incidents but actually close deals without completing security and privacy assessments on their chosen vendors.
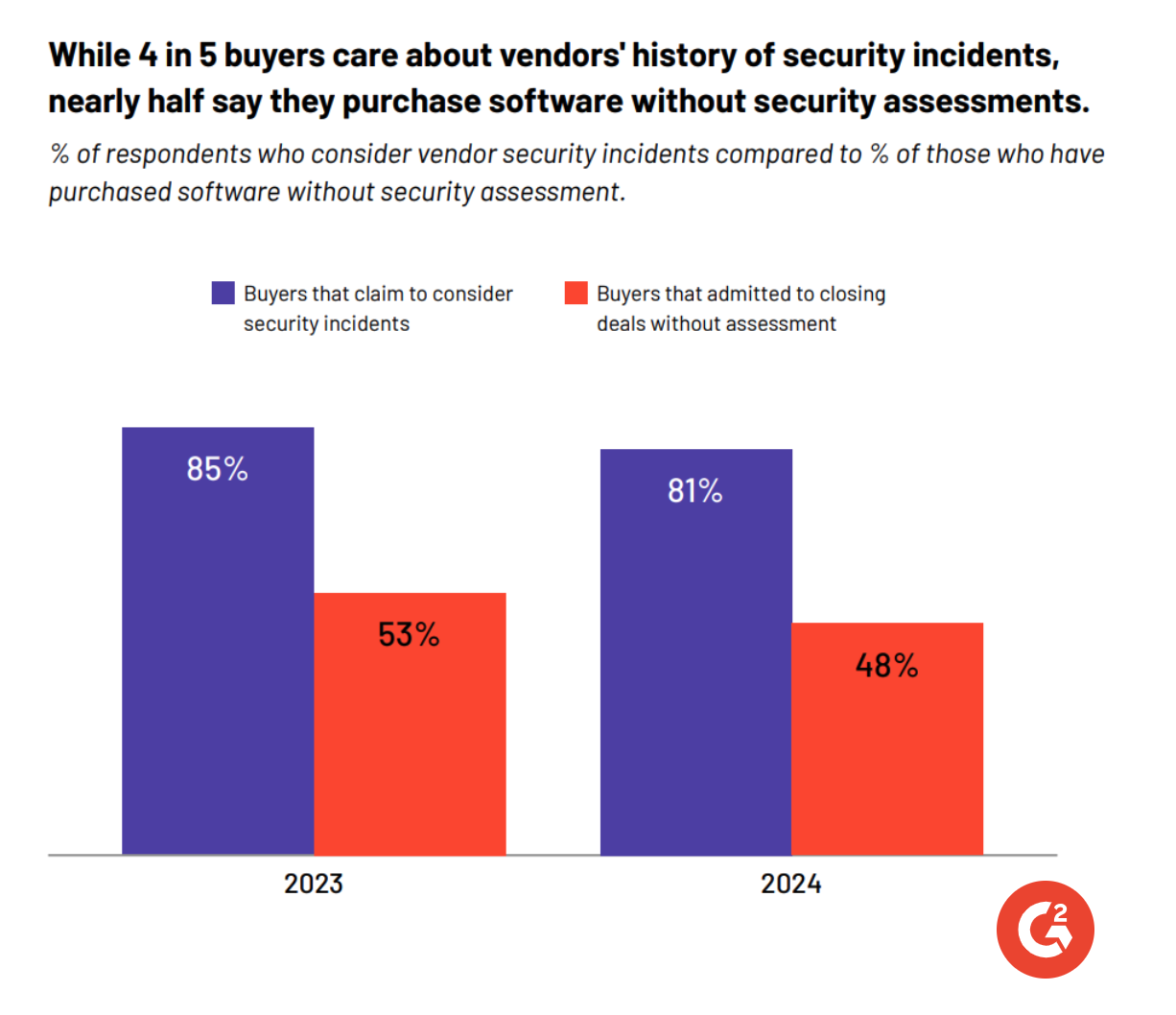
By creating this new category for zero trust platforms, G2 is taking the first step in helping buyers on their purchasing journey and ensuring security is a part of every conversation.
Be like Mira
Zero trust is here to stay. In a world where security conversations are more important than ever, the zero trust security model is here to change the game by ensuring strict verification for every user and device, whether inside or outside an organization.
Make no mistake: Zero trust may have been a “concept” a few years ago, but it needs to be a part of your security conversations now.
I started this blog with a lovely picture of Mira, who loves to bark at everything. Even if she knows who you are, she will always bark to make sure she can verify that it's really you. Mira is applying the concept of zero trust without knowing it, and it's time organizations truly understand how critical zero trust is.
Mira knows it, and now you know it too.
Learn more about zero trust, SSE, and SASE to take control of your security strategy!
Edited by Jigmee Bhutia
.png?width=500&name=G2CR_B209_Zero_Trust_Platforms_V1a%20(1).png)
.png?width=500&name=G2CR_B209_Zero_Trust_Platforms_V1a%20(1).png)
 by Dr. Chase Cunningham
by Dr. Chase Cunningham
 by Rachana Hasyagar
by Rachana Hasyagar
 by Preethica Furtado
by Preethica Furtado